Network Communication and Ports
Depending on what version of Palette you are using, the internal architecture and network communication will be different. Before Palette 4.0.0 the management platform communicated with the workload cluster via NATS. Starting with Palette 4.0.0, the management platform communicates with the workload cluster via gRPC. Use the tabs below to view the network communication and ports for each architecture.
SaaS Network Communications and Ports
- gRPC
- NATS
The following ports must be reachable from a network perspective for Palette SaaS to function correctly.
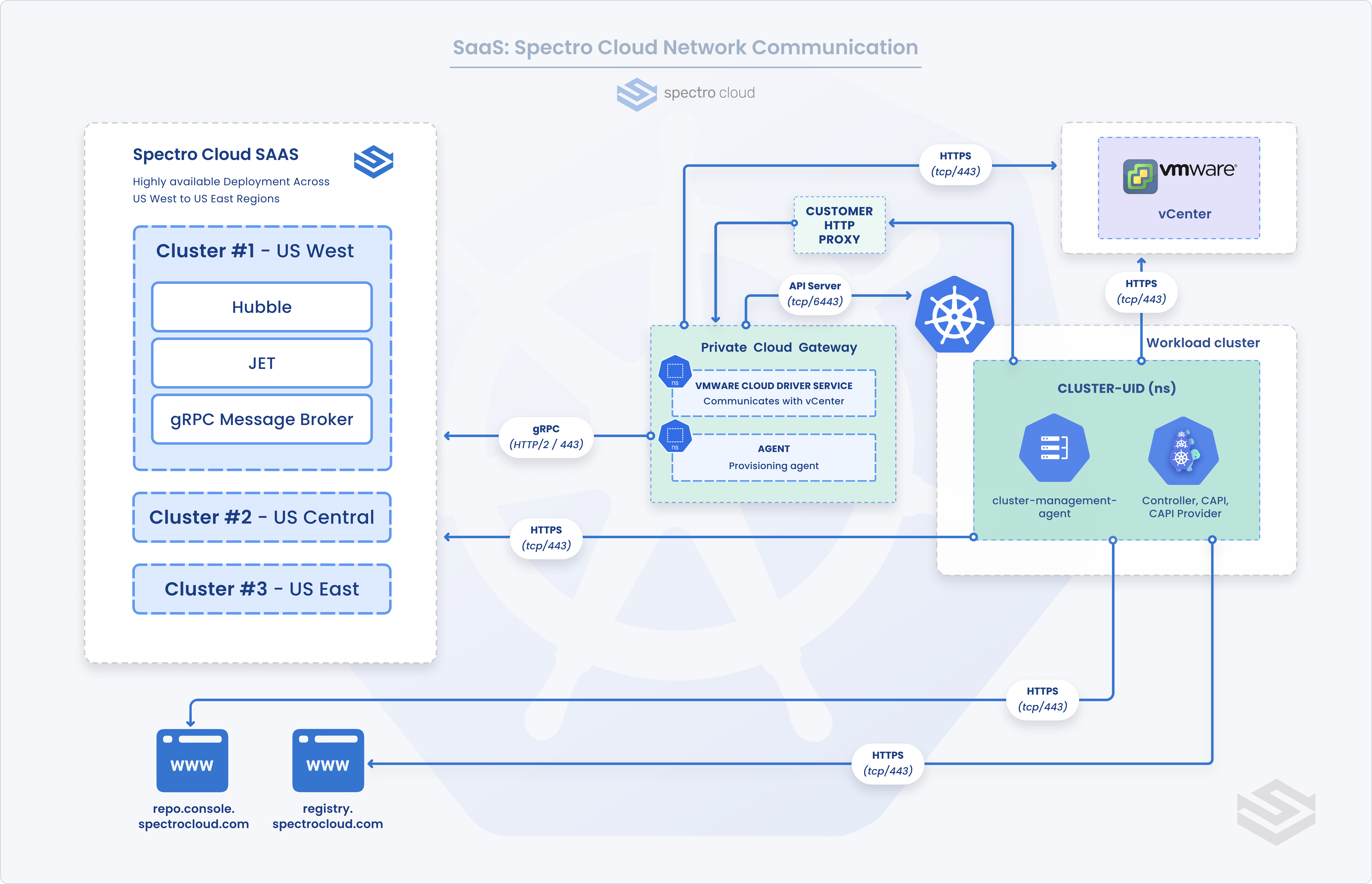
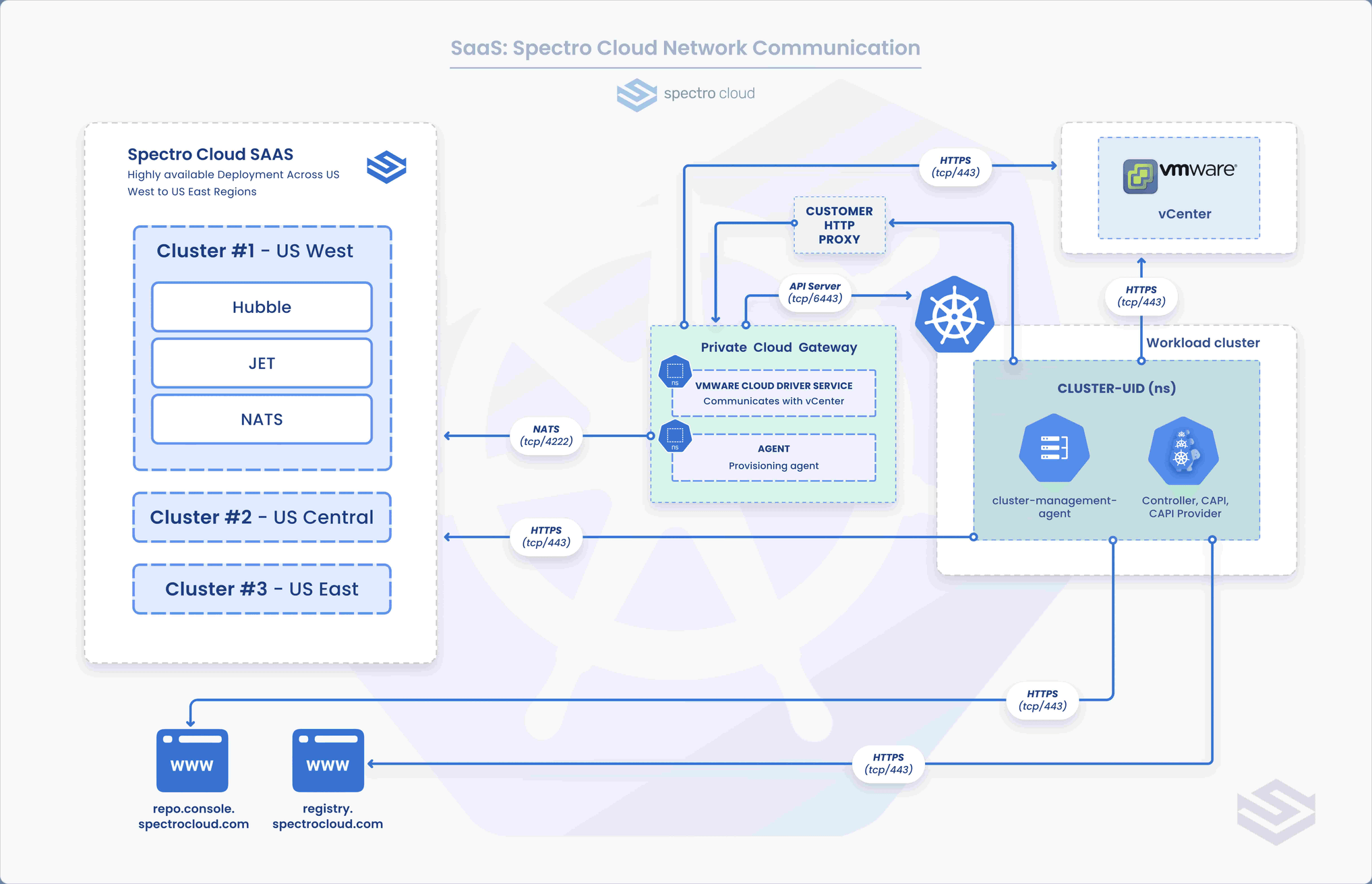
The following ports must be reachable from a network perspective for Palette SaaS to function correctly.
SaaS Managed With Edge
- gRPC
- NATS
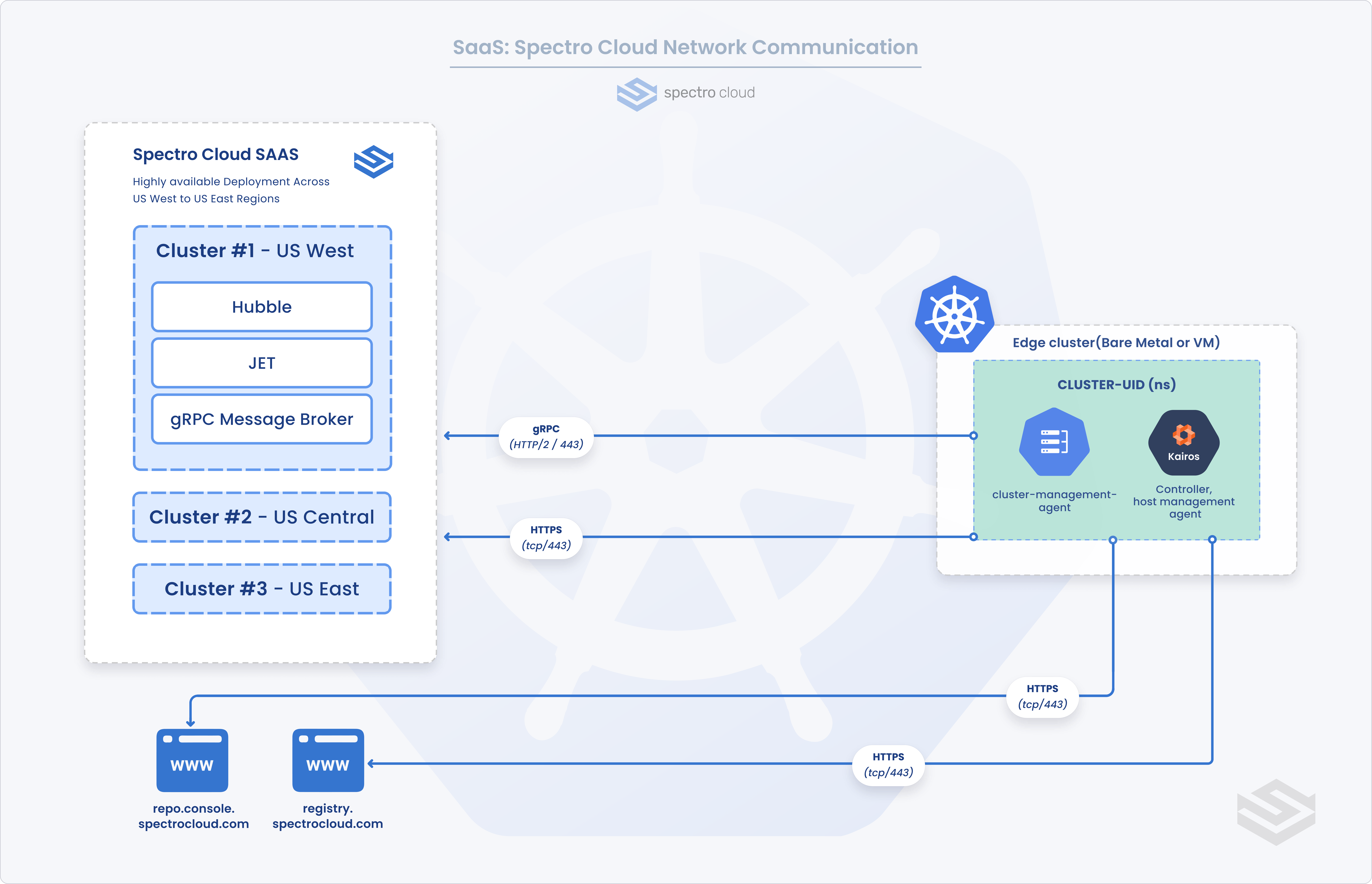
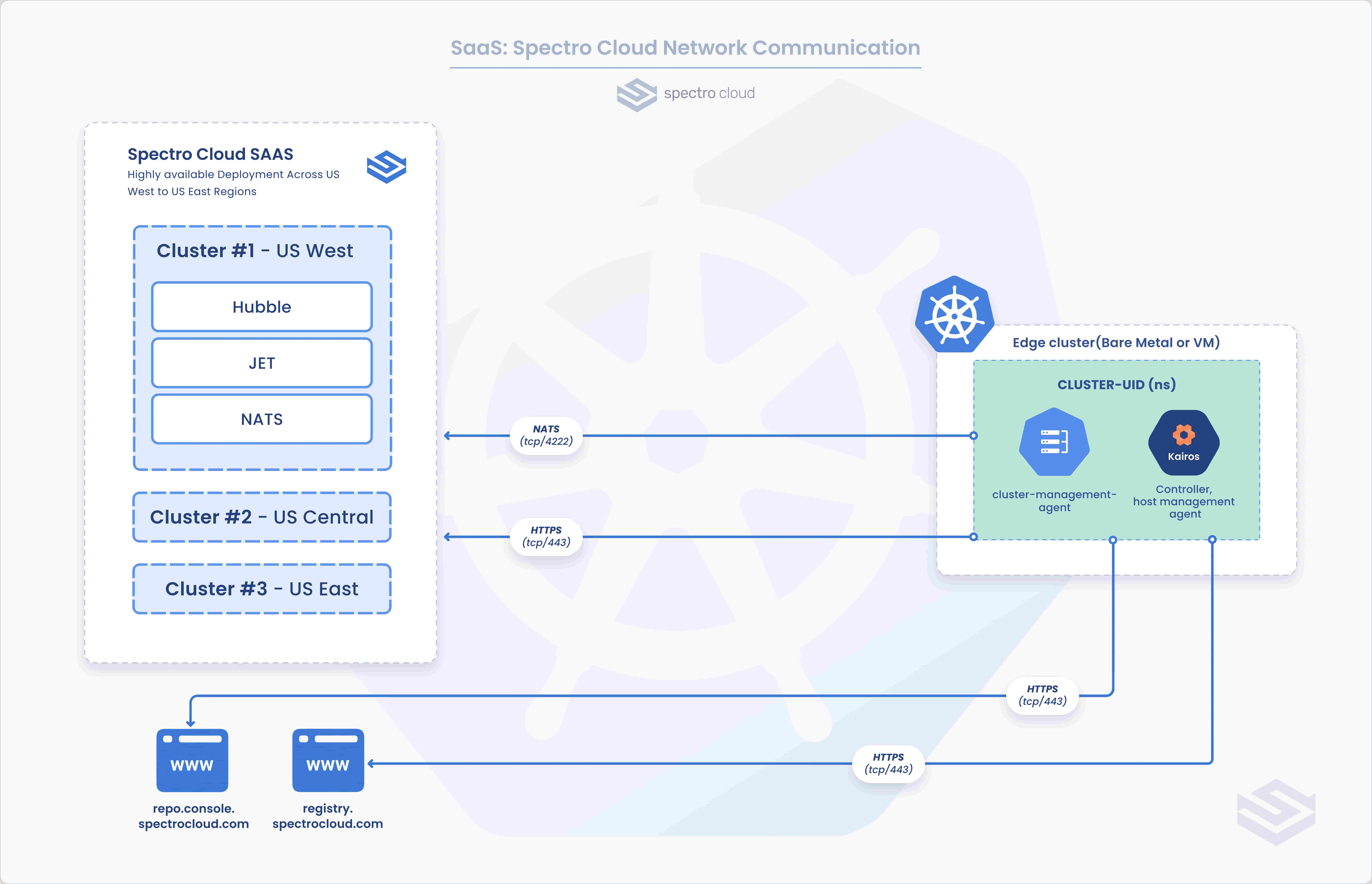
Network Ports
The following ports must be reachable from a network perspective for Palette to operate properly.
- gRPC
- NATS
Management Platform
| Port | Direction | Purpose |
|---|---|---|
| HTTPS (tcp/443) | INBOUND | Browser/API access to management platform . |
| HTTPS (tcp/443) | INBOUND | gRPC communication between Palette and the workload cluster. |
| NATS (tcp/4222) | INBOUND | Agent running inside connecting to management platform [Deprecated] |
Workload Cluster
| Port | Direction | Purpose |
|---|---|---|
| HTTPS (tcp/443) | OUTBOUND | API access to management platform and gRPC |
| HTTPS (tcp/443) | OUTBOUND | gRPC, Registry (packs, integrations), Pack containers, Application Updates |
| NATS (tcp/4222) | OUTBOUND | Registry (packs, integrations), Pack containers, Application Updates [Deprecated] |
Management Platform
| Port | Direction | Purpose |
|---|---|---|
| HTTPS (tcp/443) | INBOUND | Browser/API access to management platform |
| NATS (tcp/4222) | INBOUND | Agent running inside connecting to management platform |
Workload Cluster
| Port | Direction | Purpose |
|---|---|---|
| HTTPS (tcp/443) | OUTBOUND | API access to management platform |
| NATS (tcp/4222) | OUTBOUND | Registry (packs, integrations), Pack containers, Application Updates |
| NATS (tcp/4222) | OUTBOUND | Registry (packs, integrations), Pack containers, Application Updates |
You can expose inbound port 22 for SSH if you would like to access your cluster nodes for troubleshooting remotely. This is entirely optional and not required for Palette to operate appropriately.
Self-Hosted Network Communications and Ports
- gRPC
- NATS
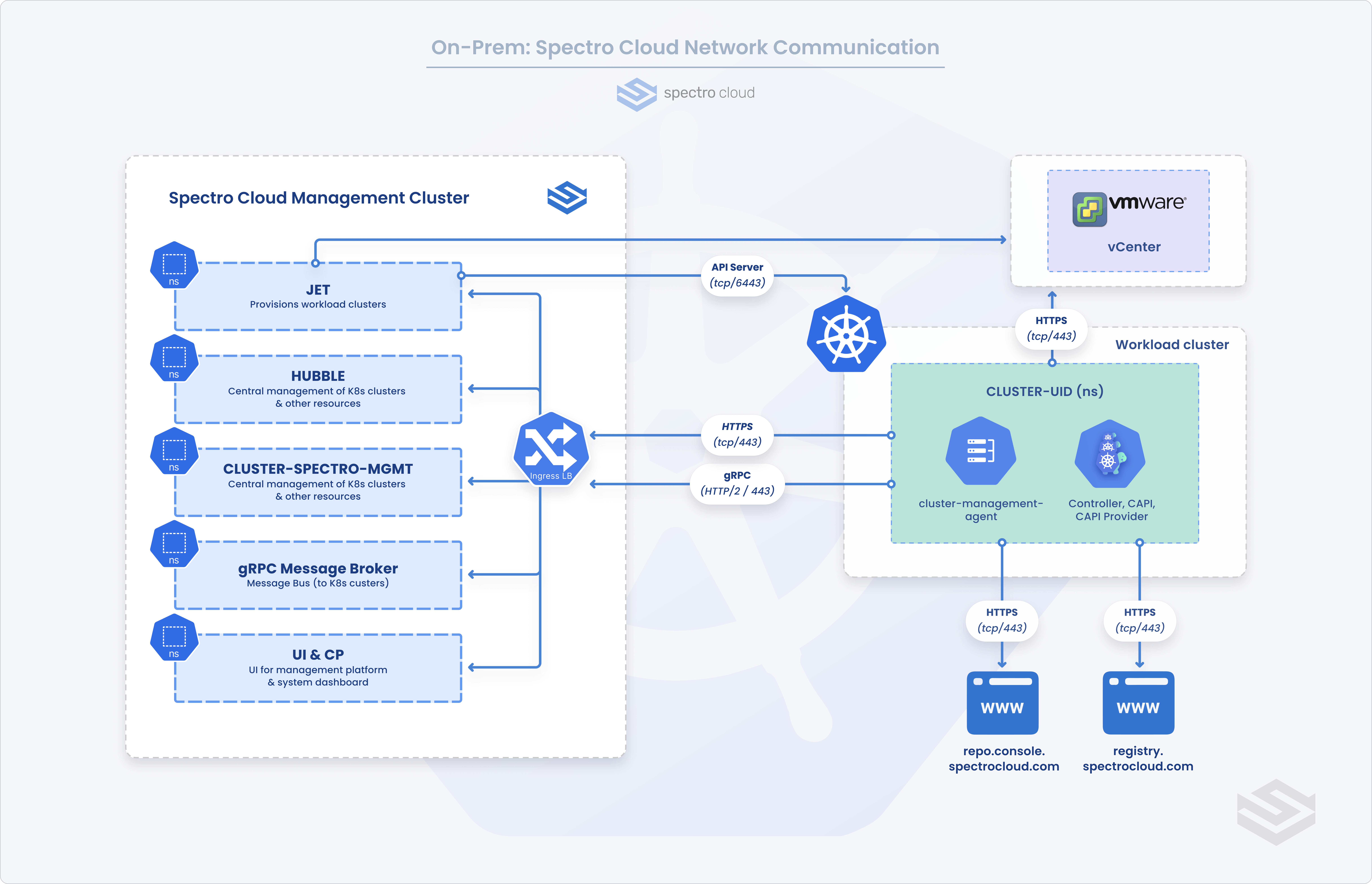
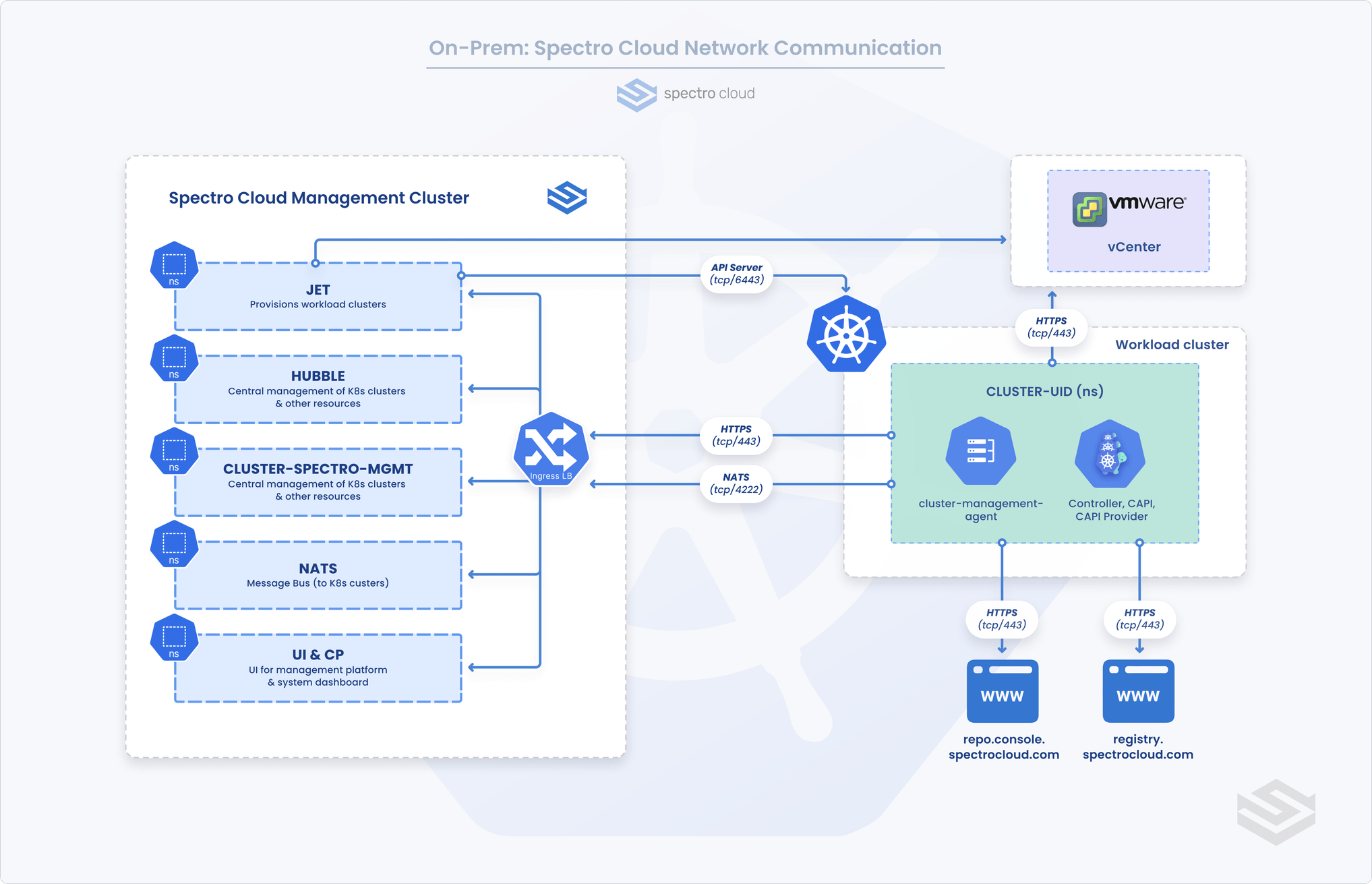
The following ports must be reachable from a network perspective for Palette self-hosted to function correctly.
- gRPC
- NATS
Management Platform
| Port | Direction | Purpose |
|---|---|---|
| HTTPS (tcp/443) | INBOUND | Browser/API access to management platform, gRPC |
| NATS (tcp/4222) | INBOUND | Message Bus for workload clusters [Deprecated] |
| HTTPS (tcp/443) | OUTBOUND | vSphere vCenter API, Registry (packs, integrations), Pack containers, app updates, gRPC |
| HTTPS (tcp/6443) | OUTBOUND | Workload K8s cluster API Server |
Workload Cluster
| Port | Direction | Purpose |
|---|---|---|
| HTTPS (tcp/443) | OUTBOUND | API access to management platform |
| NATS (tcp/4222) | OUTBOUND | Agent communication via message bus [Deprecated] |
| HTTPS (tcp/443) | OUTBOUND | vSphere vCenter API, gRPC, Registry (packs, integrations), Pack containers, Application updates |
Management Platform
| Port | Direction | Purpose |
|---|---|---|
| HTTPS (tcp/443) | INBOUND | Browser/API access to management platform |
| NATS (tcp/4222) | INBOUND | Message Bus for workload clusters |
| HTTPS (tcp/443) | OUTBOUND | vSphere vCenter API, Registry (packs, integrations), Pack containers, app updates. |
| HTTPS (tcp/6443) | OUTBOUND | Workload K8s cluster API Server |
Workload Cluster
| Port | Direction | Purpose |
|---|---|---|
| HTTPS (tcp/443) | OUTBOUND | API access to management platform |
| NATS (tcp/4222) | OUTBOUND | Agent communication via message bus |
| HTTPS (tcp/443) | OUTBOUND | vSphere vCenter API, Registry (packs, integrations), Pack containers, Application updates |
You can expose inbound port 22 for SSH if you would like to access your cluster nodes for troubleshooting remotely. This is entirely optional and not required for Palette to operate appropriately.